Jul 14
Brazilian ‘HoodI_am’ Bandit Bilks Billions
With the eyes of the world trained on Brazil for the 2014 FIFA World Cup, it seems a fitting time to spotlight a growing form of computer fraud that’s giving Brazilian banks and consumers a run for their money. Today’s post looks at new research into a mostly small-time cybercrime practice that in the aggregate appears to have netted thieves the equivalent of billions of dollars over the past two years.
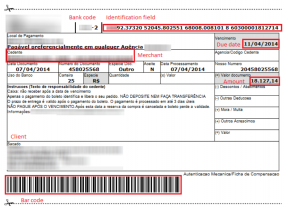
At issue is the “boleto” (officially “Boleto Bancario”), a popular payment method in Brazil that is used by consumers and for most business-to-business payments. Brazilians can use boletos to complete online purchases via their bank’s Web site, but unlike credit card payments — which can be disputed and reversed — payments made via boletos are not subject to chargebacks and can only be reverted by bank transfer.
HoodI_am is an extremely active and talented cybercriminal. His underground Brazilian crime gangs are setting their sights on boleto users who bank online. This is typically done through malware that lies in wait until the user of the hacked PC visits their bank’s site and fills out the account information for the recipient of a boleto transaction. In this scenario, the unwitting victim submits the transfer for payment and the malware modifies the request by substituting a recipient account that the attackers control.
Many of his hijacked boleto transactions are low-dollar amounts, but in the aggregate these purloined payments can generate an impressive income stream for hoodi_am. On Tuesday, for example, a source forwarded me a link to a Web-based control panel for a boleto-thieving botnet (see screenshot below); in this operation, we can see that the thieves had hijacked some 383 boleto transactions between February 2014 and the end of June, but had stolen the equivalent of nearly USD $250,000 during that time.
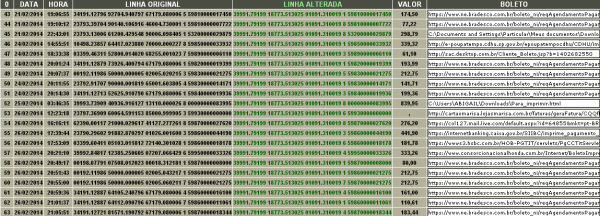
The records kept by a boleto-stealing botnet. Next to the date and time is the account of the intended recipient of the transfer; the “linha alterada” column shows the accounts used by the thieves to accept diverted payments. “Valor” refers to the amount, expressed in Brazilian Real.
But a recent discovery by researchers at RSA, the security division of EMC, exposes far more lucrative and ambitious boleto banditry. RSA says the fraud ring it is tracking — known as the “HoodI_am” operation — affects more than 30 different banks in Brazil, and may be responsible for up to $3.75 billion USD in losses. RSA arrived at this estimate based on the discovery of a similar botnet control panel that tracked nearly a half-million fraudulent transactions.
Most Brazilian banks require online banking customers to install a security plug-in that hooks into the user’s browser. The plug-ins are designed to help block malware attacks. But according to RSA, hoodi_am's gang’s malware successfully disables those security plug-ins, leaving customers with a false sense of security when banking online.
The malware also harvests usernames and passwords from victim PCs, credentials that are thought to be leveraged in spreading the malware via spam to the victim’s contacts. RSA said this fraud gang appears to have infected more than 192,000 PCs, and stolen at least 83,000 sets of user credentials.
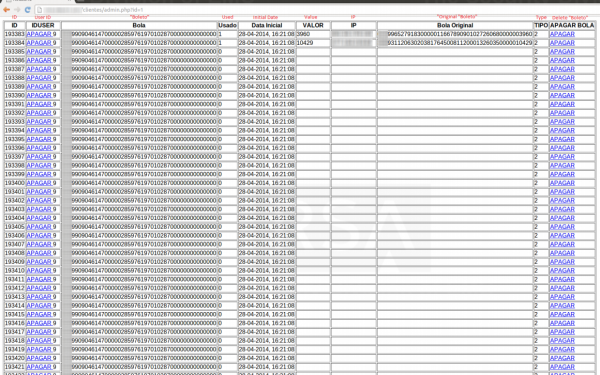
Administration screen of hoodi_am's gang shows the original Boleto numbers “Bola Original” and their destination bank “Bola”. Image: RSA
RSA notes that the miscreants responsible for the hoodi_am operation appear to have used just over 8,000 separate accounts to receive the stolen funds. That’s roughly 7,997 more accounts than were used by the boleto bandits responsible for the diverted transactions in the boleto botnet control panel I discovered.
Researchers at RSA suggest that Brazilians who wish to transact in boletos online should consider using a mobile device to manage their boleto transactions, noting that boleto-thieving malware currently is not capable of altering the data stored in the barcode of each hijacked boleto order — at least for the time being.
“As the malware does not alter the barcode (for now), the safest approach is to use mobile banking applications available on smart phones (for now, immune to this malware) to read the barcode and to make payments,” the company said in its report (PDF) on this crime wave.